The following will walk you through configuring the FVL328 and Windows 2000 Prof/Server and XP for VPN.
Wednesday, August 31, 2005
ROUTER STATUS
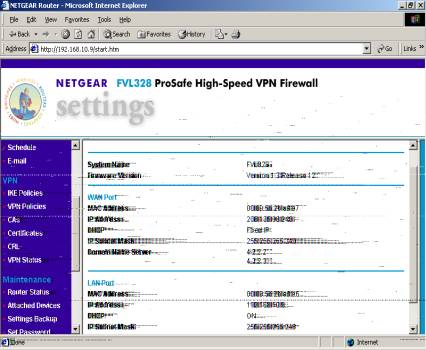
A. Please obtain the following information for Proper VPN configuration.
Firmware Version and Release (this may be important if a possible bug is encountered)(The firmware version here is 1.3 release 12)
WAN IP and Mask Address. (206.135.38.248)
LAN IP (192.168.10.9) and Mask Address (255.255.255.0). (An attached devices IP Address will be used & not the FVL328’s LAN IP)
Proceed to Attached devices an obtain an IP from the list, then proceed to IKE Policy.
IKE POLICY
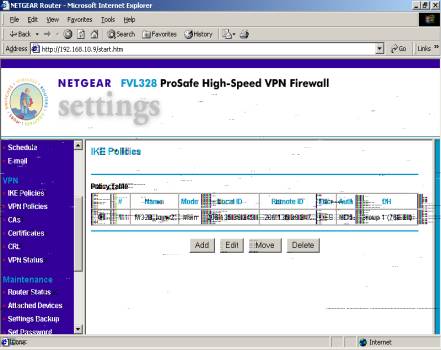
B. Proceed and select ‘ADD.’
返回
IKE POLICY CONFIGURATION
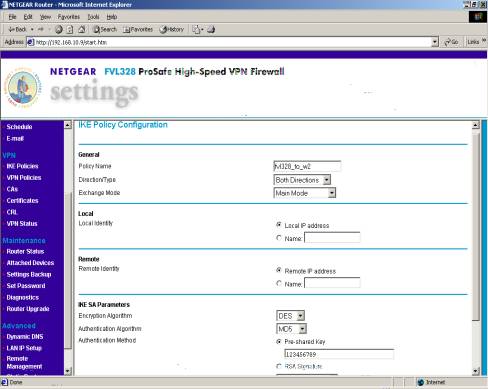
Cont.
C.IKE Policy Configuration
The Policy Name is for your reference only and not crucial to establishing a VPN connection.
Please specify the ‘Direction Type’ as ‘Both.’
Please specify the ‘Exchange Mode’ as ‘Main Mode.’
Please specify the ‘Local Identity as ‘Local IP Address.’
Please specify the ‘Remote Identity as ‘Remote IP Identity.’
Please specify the ‘Encryption Algorithm’ as ‘DES.’
Please specify the ‘Authentication Algorithm’ as MD5.’
Please select ‘Pre-Shared Key’ for ‘Authentication Method’ and specify a key such as ‘123456789 (without the quotes and period).’
Please select ‘APPLY’.
VPN Policies
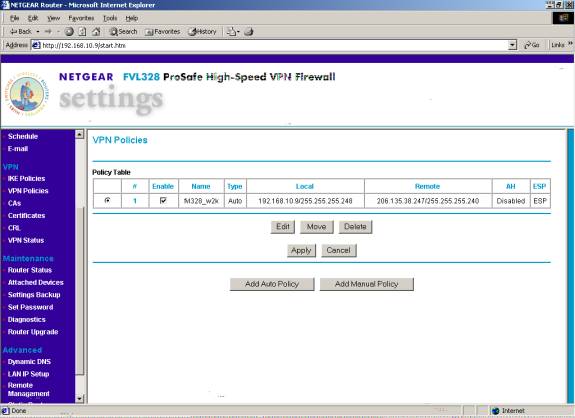
D. Please select ‘Add Auto Policy.’ The Policy in this screen shot is what the policy will look like after we configure the policy.
AUTO VPN POLICY CONFIGURATION
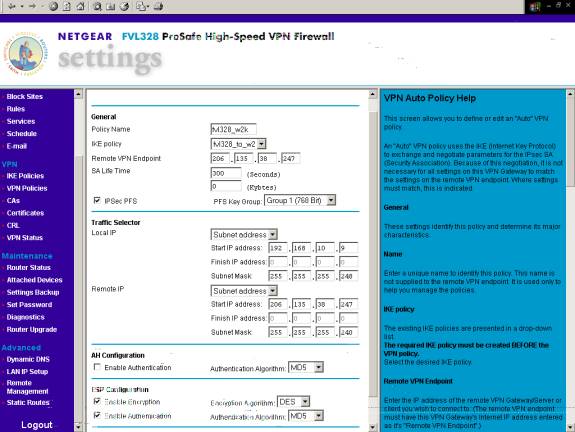
E. Auto VPN policy
Please specify a Policy Name. The ‘Policy Name’ is for your reference only.
Please select the correct IKE Policy, which in this case is the IKE policy Name we just created.
Please specify the ‘Remote VPN Endpoint’ as the Remote WAN’s IP address.
Please select and check IPSec PFS and select Group 1 (768 Bit) for the PFS Key Group.
Please specify the ‘Local IP’ under ‘Traffic Selector’ as ‘Subnet Address’ and specify the Local LAN IP and Mask address of the FVL328 accordingly.
Please specify the ‘Remote IP’ under ‘Traffic Selector’ as ‘Subnet Address’ and specify the Remote LAN IP and Mask address if a router is used on the remote site and the WAN IP and Mask Address if the Remote is connected directly to the Internet without a Router.
Now, we will check and enable Encryption, and Authentication. under ESP Configuration.
Please specify ‘Encryption Algorithm’ as ‘DES,’ and ‘Authentication Algorithm’ as ‘MD5.’
VPN STATUS
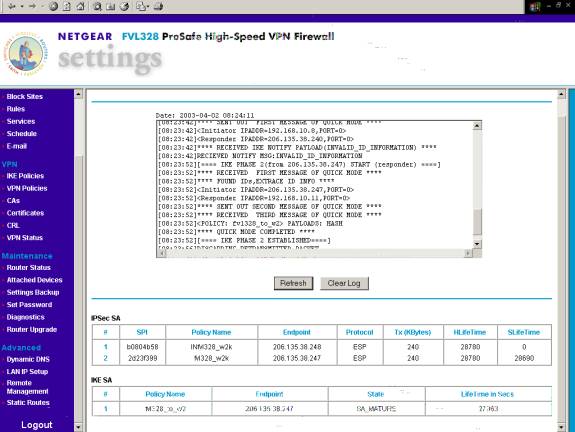
F. VPN Status
The above screen shot displays the logs and the IPSec and IKE SA that is displayed when a VPN Tunnel is established successfully.
Windows 2000, XP Local Security Settings
G. Local Security Policy is located at:
Start.
Control Panel.
Administrative Tools.
Local Security Policy.
H. Local Security Settings.
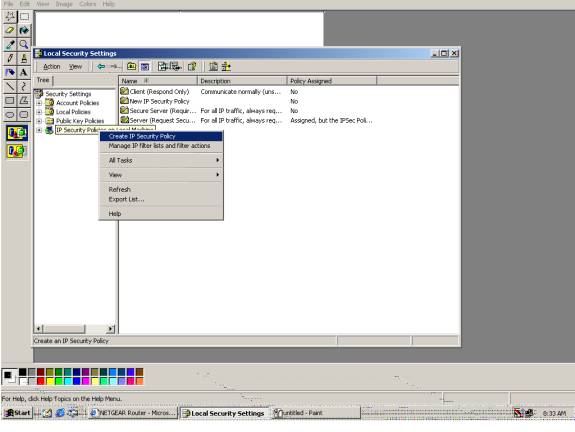
Right click on IP Security Policies on Local Machine.
Select and click on Create IP Security Policy.
IP Security Policy Wizard
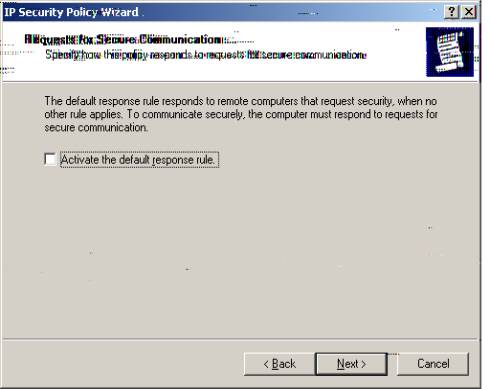
I. Uncheck to ‘Activate the default response rule.’
IP Security Policy Name
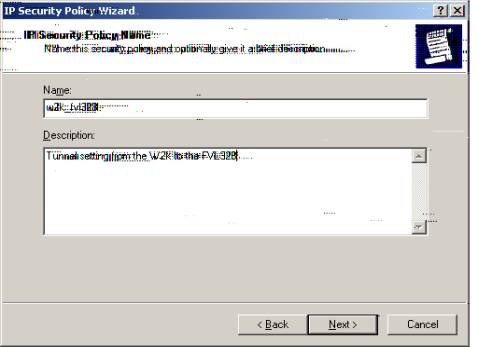
J. Enter a ‘Name’ for the Policy, for example: “w2k_fvl328.”
K. The Description above was entered for Policy Description only and it states:
“Tunnel settings from the W2k to the FVL328.”
W2k_FVL328 Policy
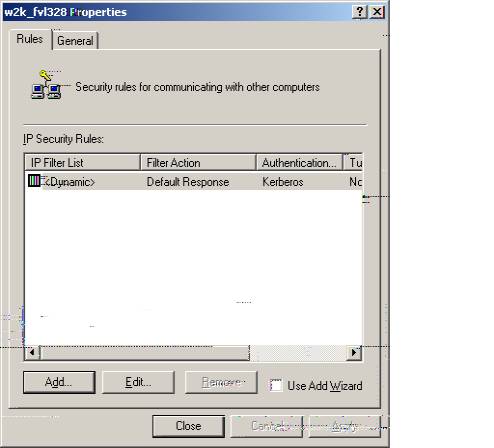
L. Now we will create an IP security Rule for each tunnel one at a time as follows.
Select ‘Add.’
New Rule Properties for W2k_FVL328
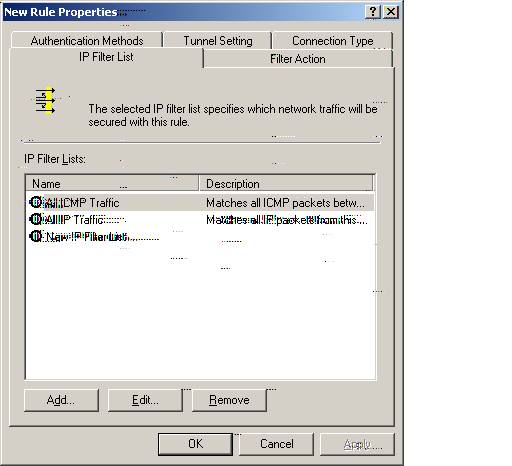
M. Please select ‘New IP Filter List’ and Select ‘Add.’
IP Filter List for W2k_FVL328
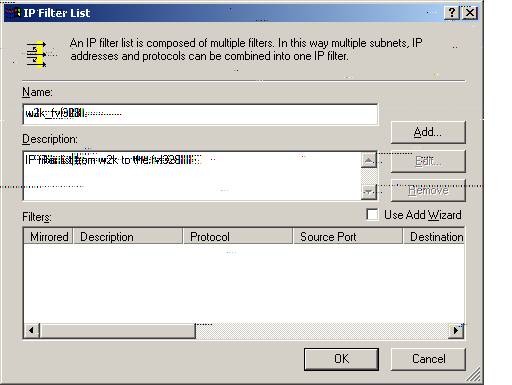
N. Specify the Name as ‘w2k_fvl328.’ The description we entered for description only as ‘IP Filter List from w2k to the fvl328.’
Select ‘Add.’
IP Filter List Properties for W2k_FVL328
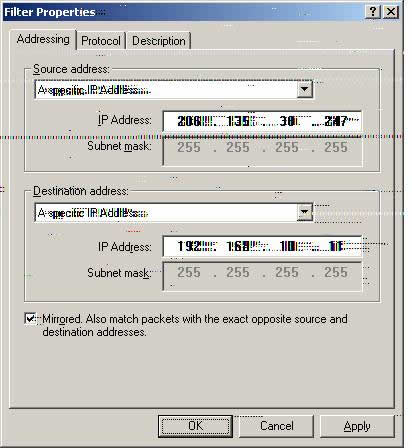
O. The Source address is set to ‘A specific IP Address.’
Please set the IP address accordingly.
Example: IP address is the WAN IP of the w2k system (206.135.38.247).
The Subnet mask is set to broadcast.
P. The Destination address is set to ‘A specific IP Address.’
Please set the IP address accordingly.
Example: IP address is the LAN IP (192.168.10.11) of a workstation of the LAN and not that of the LAN IP of the FVL328
The Subnet mask is set to broadcast.
Please check ‘Mirrored.’
Select ‘OK
Filter Action Properties

Q. Please select ‘Add.’
Filter Action Name for W2k_FVL328
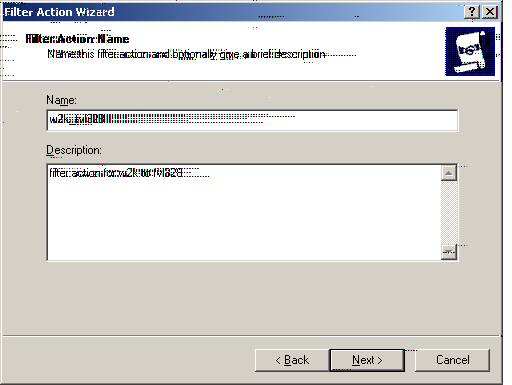
R. Specify the Name as ‘w2k_fvl328.’ The description we entered for description only as ‘Filter Action from w2k to the fvl328.’
Select ‘Next.’
Filter Action for W2k_FVL328
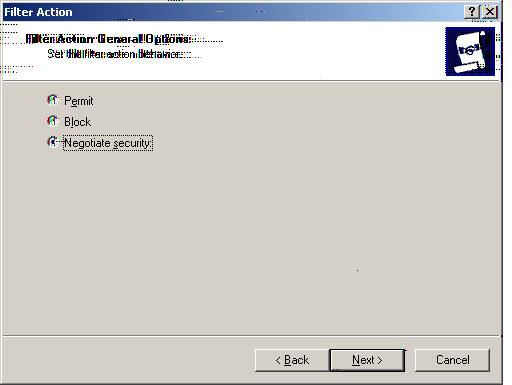
S. Please select ‘Negotiate Security’ and then select ‘Next.’
Filter Action for W2k_FVL328
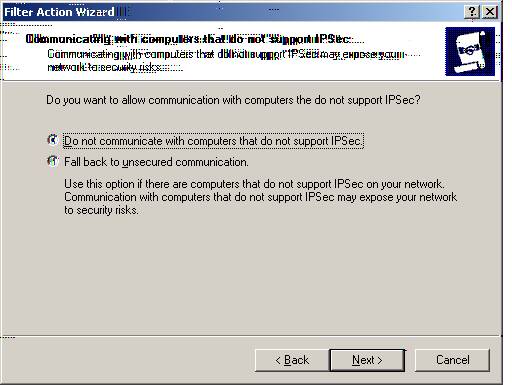
T. Please select ‘Do not communicate with computers that do not support IPSec.’
Select ‘Next.’
W2k_FVL328 Security Method
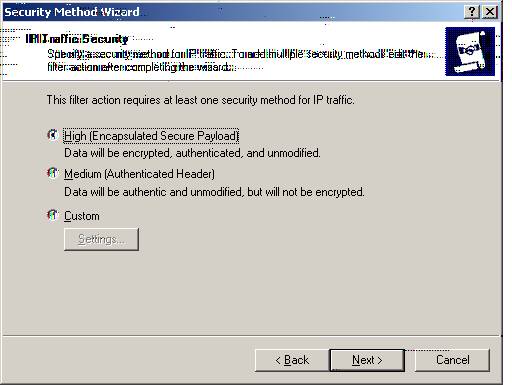
U. Please select High (Encapsulated Secure Payload) Data will be encrypted, authenticated, and modified.
Select ‘Next.’
W2k_FVL328 Security Method Properties
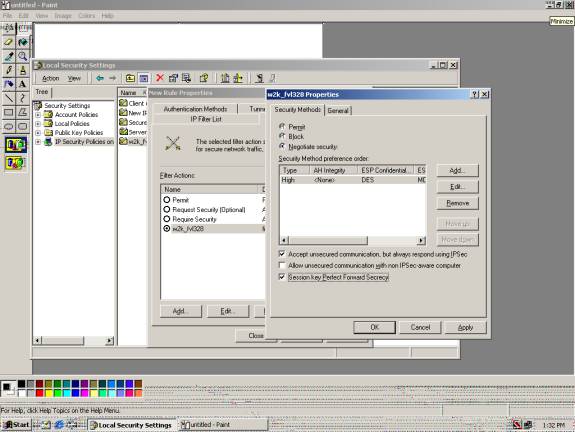
V. We should now be at the New Rule Properties with w2k_fvl328 checked under ‘Filter Action.’
Double click on the w2k_fvl328 Filter Action Rule.
w2k_fvl328 properties is displayed as above.
Please make sure that ‘Accept unsecured communication, but always respond using IPSec’ is checked, and that ‘Session key_Perfect Forward Secrecy’ is checked also.
Select ‘OK
W2k_FVL328 Connection Type
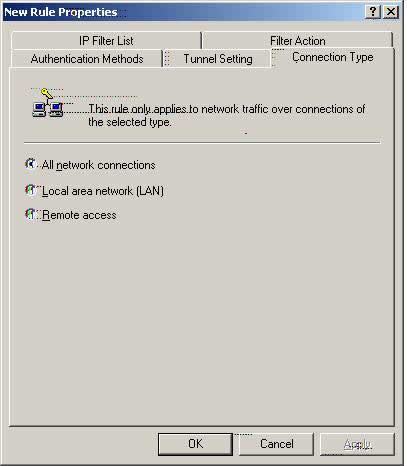
W. Please select ‘Connection Type’ and make sure that ‘All network connections’ is selected.
Select ‘Apply.’
W2k_FVL328 Tunnel Setting
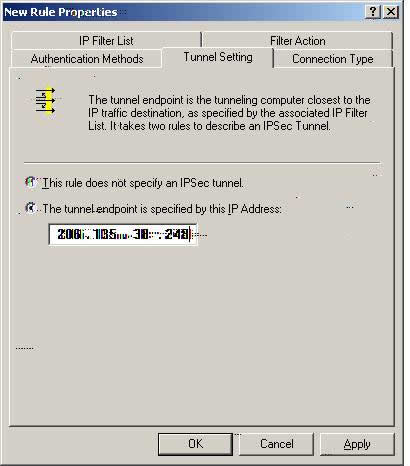
X. Please select ‘Tunnel Setting” and select ‘The tunnel endpoint is specified by this IP Address.’ Please enter the IP Address of the WAN of the FVL328 (in this case: 206.135.38.248).
Select ‘Apply.’
W2k_FVL328 Authentication Methods
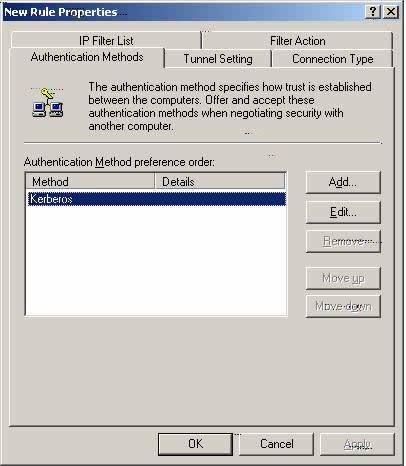
Y. Please select ‘Authentication Methods’ and highlight ‘Kerberos’ and select ‘Add.’
W2k_FVL328 Authentication Method Properties
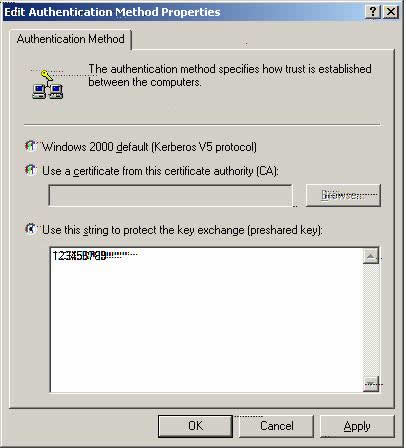
Z. Please select ‘Use the string to protect the key exchange (preshared key).’
Type the following digits: 123456789 (I use these digits as an example and for testing purposes only. You may use a different digit format).
Select ‘OK.’
W2k_FVL328 Authentication Method Main Display after configuration
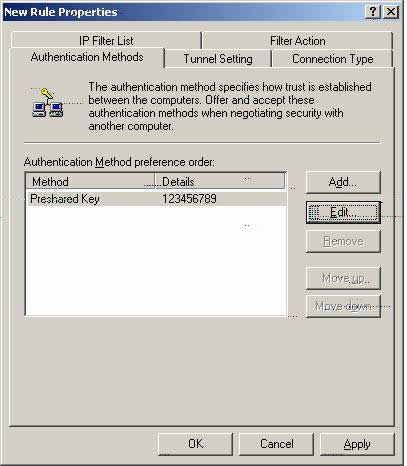
Z1. The display above is a display of the Authentication Method once it is configured.
Select ‘OK.’
W2k_FVL328 Properties
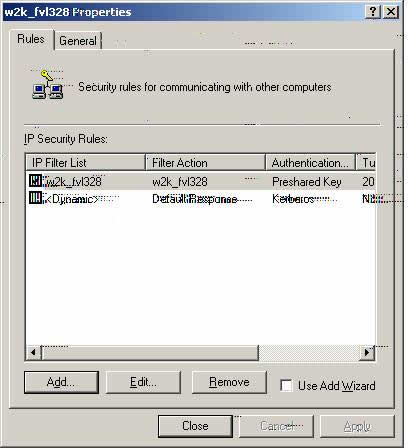
Z2. We will now create the Security Policy from the FVL328 to the W2k. A Security Policy is needed from both directions in-order to establish successfully.
Select ‘Add.’
IP Filter List Creation for FVL328_W2k
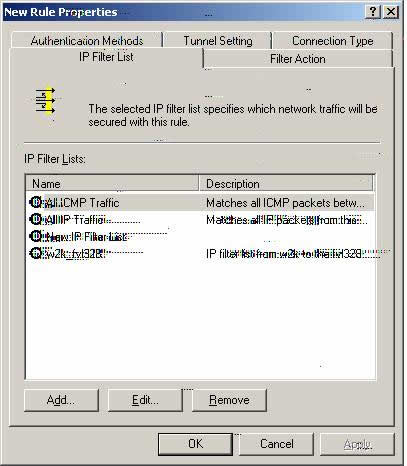
Z3. Please be sure that ‘New IP Filter List’ is checked and then select ‘Add.’
IP Filter List for FVL328_W2k
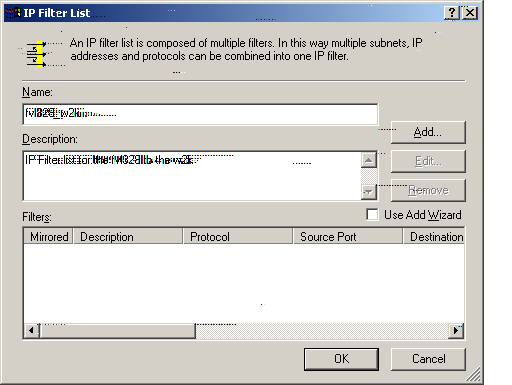
Z4. Specify the Name as ‘fvl328_w2k.’ The description we entered for description only as ‘IP Filter List from fvl328 to the w2k.’
Select ‘Add.’
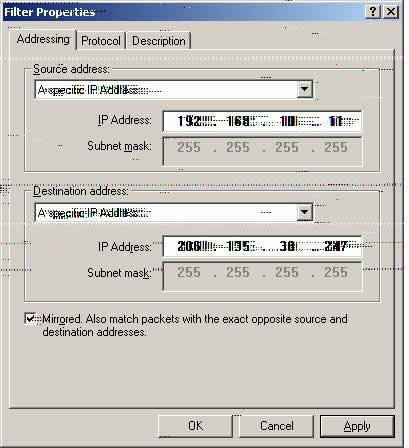
Z5. The Source address is set to ‘A specific IP Address.’
Please set the IP address accordingly.
1.Example : IP address is the LAN IP (192.168.10.11) of a workstation of the LAN and not that of the LAN IP of the FVL328.
2.The Subnet mask is set to broadcast (255.255.255.255).
Z6. The Destination address is set to ‘A specific IP Address.’
2. Please set the IP address accordingly.
Example: IP Address is the WAN IP (206.135.38.247) of the W2k system
The Subnet mask is set to broadcast (255.255.255.255).
Please check ‘Mirrored.’
Select ‘OK.’
IP Filter List after creation for FVL328_W2k
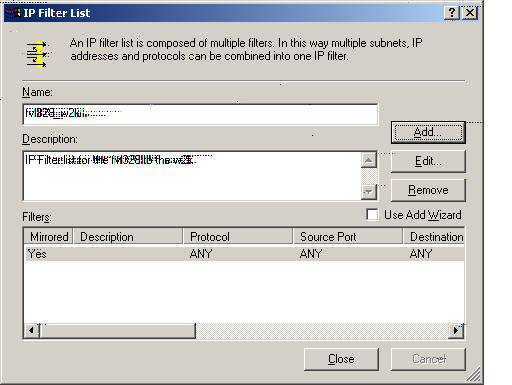
Z7. Select ‘Close.’
New Rule Properties for the FVL328_W2k
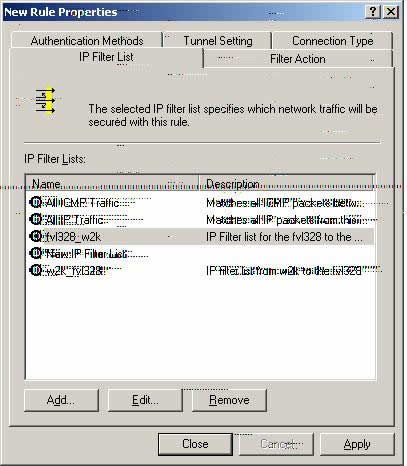
Z8. Please select fvl328_w2k in the IP Filter List and then select the ‘Filter Action’ tab.
Filter Action Properties for FVL328_W2k
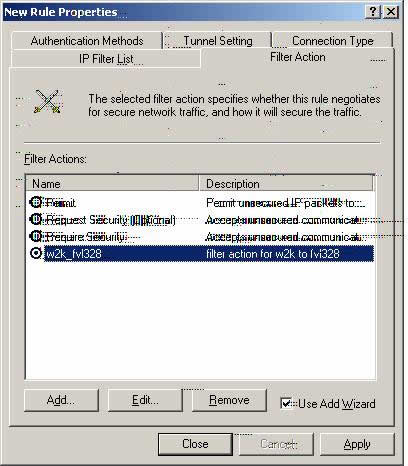
Z8. Please select w2k_fvl328 and proceed to the ‘Connection Type’ tab and select ‘All network connections.’(We will use the w2k_fvl328 configuration for all the authentication methods. They are the same both ways). Proceed to ‘Tunnel Setting.’
Tunnel Setting for FVL328_W2k
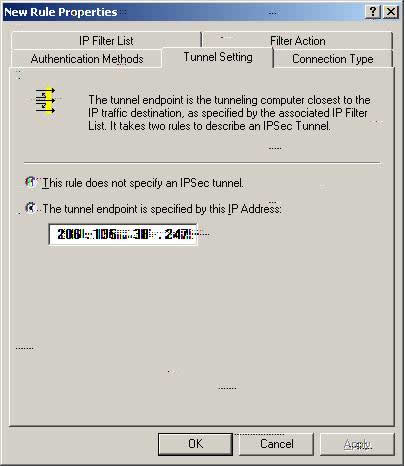
Z9. Please select ‘The tunnel endpoint is specified by this IP Address and specify the WAN IP (206.135.38.247) address of the W2k system.
Select the ‘Authentication Methods’ tab.
Authentication Methods for FVL328_W2k
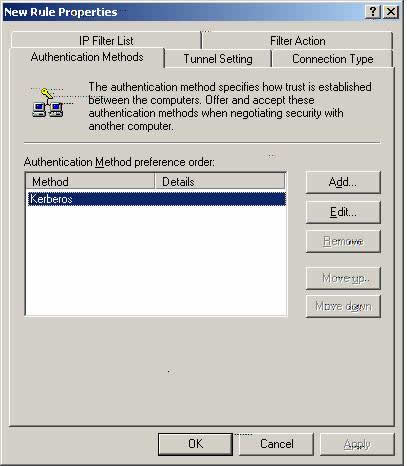
Z10. Please highlight ‘Kerberos’ and select ‘Add.’
Authentication Method Properties for FVL328_W2k
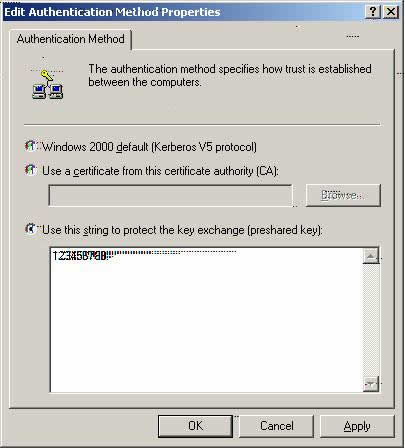
Z11. Please select ‘Use this string to protect the key exchange (preshared key)’ and input the following digits: 123456789.
1. Select ‘OK.’
Authentication Method Main display for FVL328_W2k
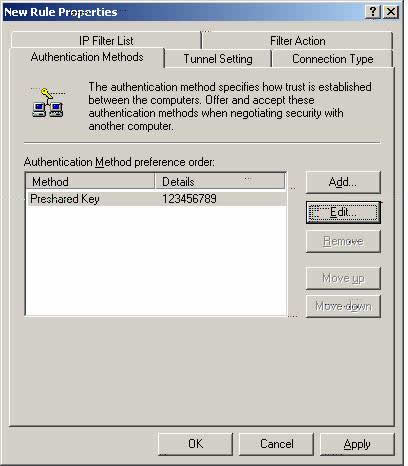
Z12. Select ‘OK.’
w2k_fvl328 & fvl328_w2k IP Security Rules main
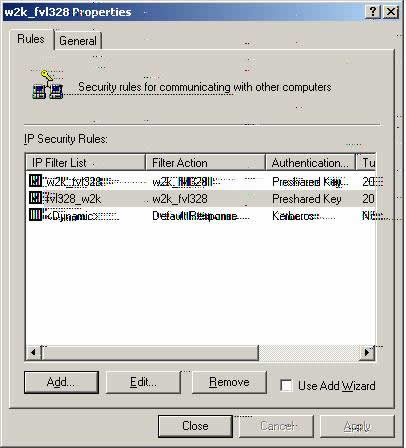
Z13. Please select the ‘General’ tab. It is not important which IP Security Rule is selected (but please makesure that both are checked) at this point.
w2k_fvl328 General Properties.
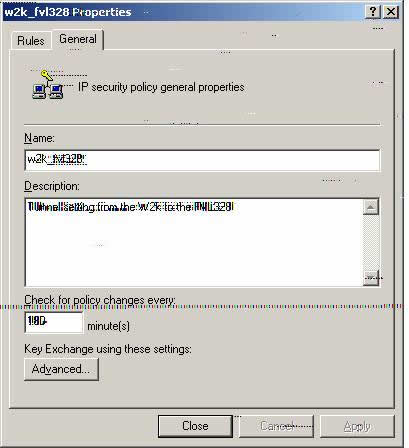
Z14. Please select ‘Advanced.’
w2k_fvl328 General/Key Exchange Settings
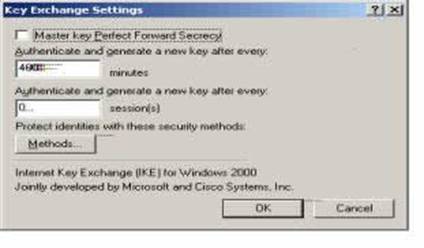
Z15. Please select ‘Methods.’
W2k_fvl328 Key Exchange Security Method
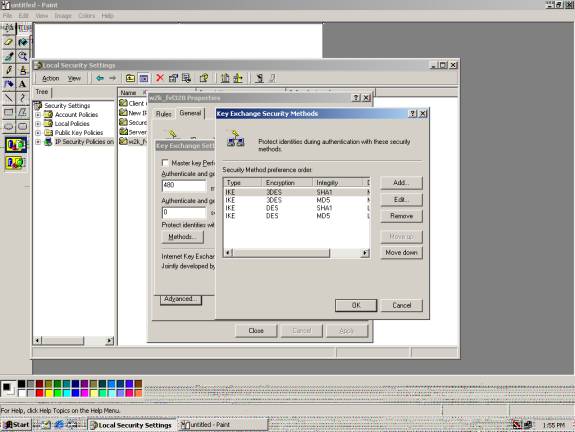
Z16. Please move up the correct Security Method Preference, which is the following:
Type = IKE
Encryption = DES
Integrity = MD5
Ditfie-Hellman Group = Low (1)
Key Exchange Security Method Main
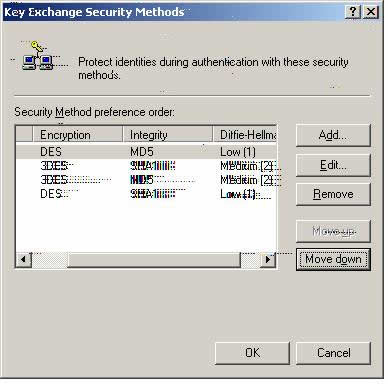
Z17. The above is the correct Security Method preference order.
Z18. Please select ‘OK, OK, Close.’
Local Security Settings Main
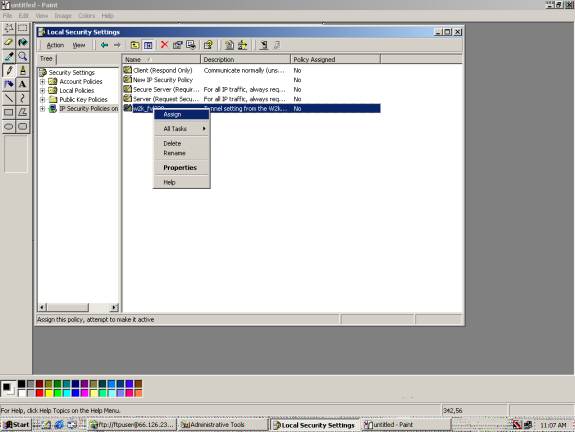
Z19. Please highlight the ‘w2k_fvl328’ Policy and right click on the policy and highlight ‘Assign.’
Local Security Settings Main
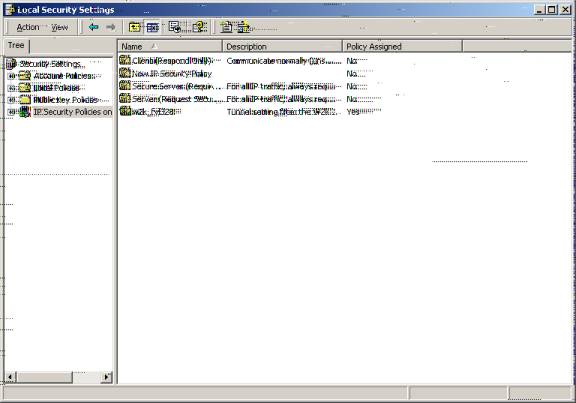
Z20. Once the w2k_fvl328 is assigned, the ‘Policy Assigned’ becomes ‘yes.’
Z21. Proceed to MS-DOS and ping the Workstation IP Address (192.168.10.11) specified in the VPN configuration.
Ping Command on the W2k system
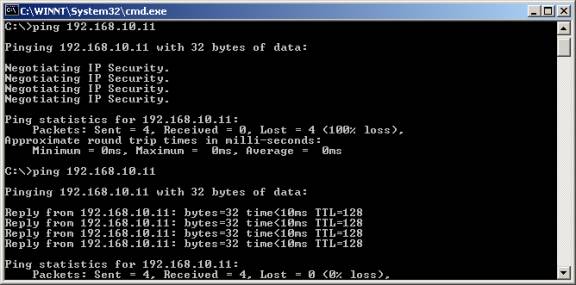
Z22. Above we have pinged the LAN IP of the workstation on the FVL328. The replies indicate successful establishment.
FVL328 VPN Status with Success
|
序号 no. |
日期 date |
作者 author |
摘要 summary |
|
1 |
2010-10-21 |
Canner.Liang |
文档创建 |
|
2 |
2010-11-26 |
Weifeng Yang |
文档校对 |
